Active Directory - Use Cases
Active Directory Domain Services is Microsoft’s Directory Server. It provides authentication and authorization mechanisms as well as a framework within which other related services can be deployed (AD Certificate Services, AD Federated Services, etc). It is an LDAP compliant database that contains objects.
In WaveMaker, you can set AD as security service provider and configure the details. There are few scenarios which need special configurations:
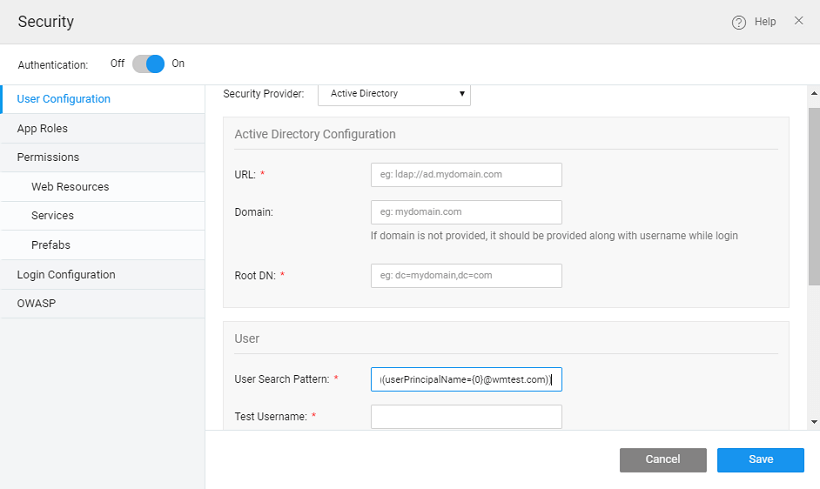
Scenario 1: Support for alternate UPN suffix in an AD domain.
In the Windows operating system's Active Directory, a User Principal Name (UPN) is the name of a system user in an e-mail address format. The user name (or "username") is followed by the "at sign (@)" and the name of the Internet domain with which the user is associated. In cases where there are multiple child domains within a parent domain, the parent domain name gets suffixed to the child domain, thus making the UPN suffix too lengthy and difficult to handle. To get over this situation, alternate UPN suffix is created and the user uses this to login.
When configuring for these situations, you need to:
- leave Domain entry blank,
- enter the Root DN following the placeholder convention "dc=example,dc=com",
- enter Test Username in the suffix email style i.e. along with the @domain.com
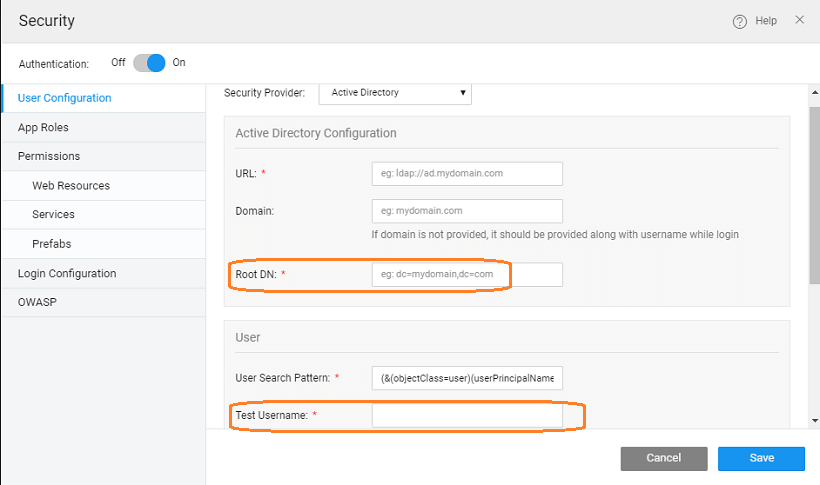 Scenario 2: Support for user search using sAMAccountName.
Scenario 2: Support for user search using sAMAccountName.
The sAMAccountName attribute is the User Logon Name used to support clients and servers from the previous version of Windows, such as Windows NT 4.0, Windows 95, Windows 98, and LAN Manager. Both userPrincipalName and sAMAccountName can be used to login to AD.
By default, WaveMaker sets the Active Directory user search to be based upon the userPrincipalName. In order to set the search based upon the sAMAccountName you need to:
- leave Domain entry blank,
- enter the User Search Pattern as:
(&(objectClass=user)(sAMAccountName={0}))
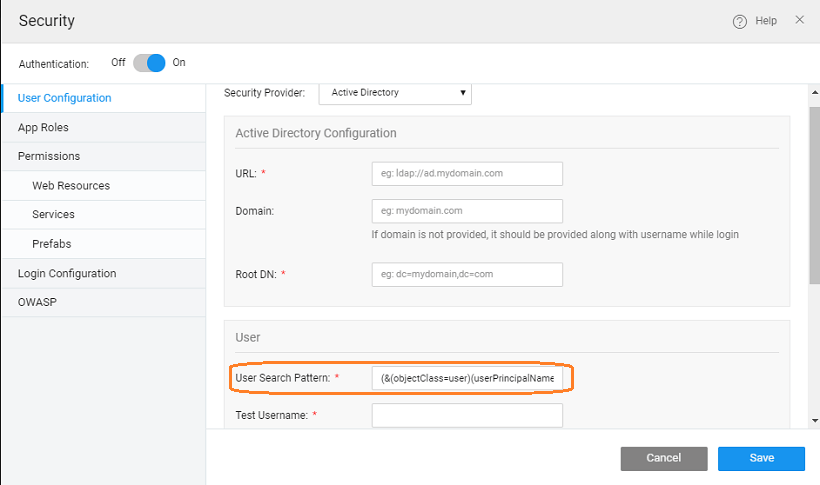 Scenario 3: Support for users with certain domain name suffix
Scenario 3: Support for users with certain domain name suffix
In order to allow access to users of a particular domain you need to:
- enter the User Search Pattern as
(&(objectClass=user)(userPrincipalName={0}@yourdomain.com))(more about search filter)
You can allow multiple domains by appending to the User Search Pattern: (&(objectClass=user)(|(userPrincipalName={0}@yourdomain.com)(userPrincipalName={0}@anotherdomain.com)))